Google, a UEFI vulnerability alarm that runs in places that users don't know about.
At The Linux Foundation's developer event "Embedded Linux Conference 2017" in the Czech Republic on October 25th, Google software engineer Ronald G.Minnich presented interesting content about UEFI firmware, which is widely used in x86 systems.
The UEFI (Unified Extensible Firmware Interface) firmware is roughly the low-level OS that governs the PC foundation. In this low-level OS, IP stack, file system, driver, Web server, own password, etc., are not freely accessible on security issues, so on x86 processors, user platform (Ring3), OS (Ring0), Then OS (Ring-1), a hypervisor like Xen, runs on "Ring-2" and "Ring-3" with more privileges than it does. Users are not aware of UEFI's movement, and its development is carried out in proprietary closed sources.
However, in recent years, the method of hackers to attack UEFI is being established. If a vulnerability is found and UEFI is rewritten as something malicious, the user is actually in a state of permanent attack without knowing the method of the vulnerability.
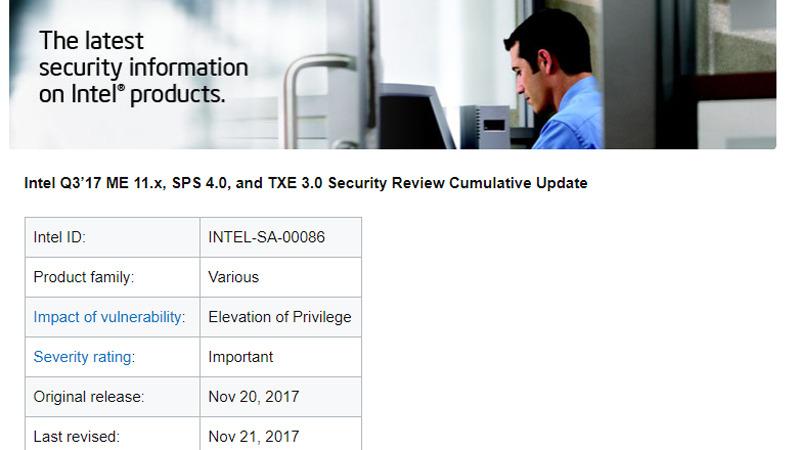
Intel Management Engine, which runs on Ring-3, is particularly deadly. In addition to having all the management functions of the network, Intel Management Engine is also in charge of the management functions of the whole PC. The PC is running even when the power is off, so if you hijack the place, the attacker will do whatever he wants.
Therefore, it is reported that Google is currently working on the "Non-Extensible Reduce Firmware:NERF" project, which will replace the UEFI. NERF has the following six purposes.
1. Reduce the harm by limiting the functionality of the firmware. Make the motion of firmware more visual 3. Remove all runtime components (but remove Web server and IP stack because it is difficult to eliminate all Intel ME) 4.UEFI 's IP stack and other drivers remove 5.ME and UEFI delete their own ability 6. 0. Let the Linux side manage flash and updates
The presentation describes how to remove some of the features of Intel ME, including filtering components of UEFI, replacing bootstraps with Linux, and rebuilding parts of UEFI.
In addition to Google, HP has been listed as a company worried about the vulnerability of UEFI, which uses a mechanism to detect / fix UEFI tampering in its legal person-oriented PC "EliteBook" series. However, such problems, not only two companies and one company, have once again recognized the need to deal with it in the industry as a whole.

![[Latest in 2022] Explanation of how to register DAZN for docomo with images | 31 days 0 yen free trial reception until April 17](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/28/22149d541c51442b38a818ab134a8cf0_0.jpeg)
!["Amaho no Sakuna Hime" celebrates its first anniversary. The Ministry of Agriculture, Forestry and Fisheries moved to allow you to experience rice farming in a depth unparalleled in the history of games.A rice farming action RPG with over 1 million units shipped worldwide [What day is it today? ]](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/28/378f9ee978fe8784d8ab439d041eee85_0.jpeg)




