Boundary defense is the limit in telework, and what do you start to aim for a "zero trast"?
With the expansion of teleworking environments, the border defense that protects only the inside of the corporate network has become unable to guarantee security.
Therefore, the Zero Trust Network (Zero Trust) has recently attracted attention.This is a concept proposed by the US Forester Research in 2010.Assuming that all networks and devices are not safe, it is basically to verify each time you access and decide whether or not.
If you can achieve a zero trade, you will be able to access safely both inside and outside the company.In the border defense using a VPN device, issues such as compression in the network band are generated.Zero Trust is expected to solve these issues.Here is a explanation of the zero trade.
アクセスごとに認証
There are two things in the case of (1) access control according to the state of (1) and (2) dynamic verifications such as users and equipment.The following configuration is considered to be realized.
ゼロトラストを実現するための構成例[画像のクリックで拡大表示]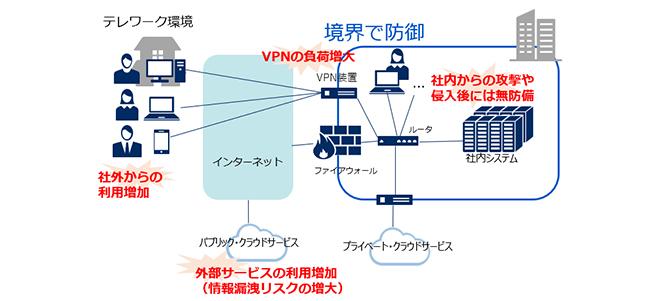
Access control determines whether or not access is possible based on the access policy set by a company every time access occurs.
For example, dynamically confirm whether the user who accesses the service has the right authority, the application that has accessed, or the authenticated device.Judge whether or not access is composed of the confirmation result and the policy.Performing this is the policy applicable point.
For the construction of policy applicable points, you can use ID -recognized proxies (IAP: IAP: IAP).ID -recognized proxy is software that replaces the service, as proxy (agency) means.
ID -recognized proxy has a function that determines access according to the ID.When accessing the service, be sure to set it to go through the ID -recognized proxy, and only access from the permitted ID.
Typical ID-recognized proxies include Microsoft's Azure Active Directory Application Proxy and Google's Identity-Aware Proxy.
Dynamic verifications such as users and equipment are equipment authentication based on user authentication and client certificate.User authentication should be implemented every time you access the service, but it is not realistic because it takes time for authentication.In fact, there are many operations such as unnecessary authentication on the day once authenticated once.
In the case of equipment authentication, not only is it simply authenticated, but also a computer condition is collected and verified.For example, whether the virus software has been updated to the latest version, where is accessing, or if an application that is not allowed by a company is installed.Calling and authenticating the operating status of such a personal computer is called "risk -based authentication".
Furthermore, save all these accesses as logs.Analyze the accumulated logs to find out whether new security risks have occurred, or if there are any services or information that requires access restrictions.And always change from the results of the analysis to the optimal policy.
It is necessary to register as a Nikkei Clostek Active member in the future
日経クロステック Activeは、IT/製造/建設各分野にかかわる企業向け製品・サービスについて、選択や導入を支援する情報サイトです。製品・サービス情報、導入事例などのコンテンツを多数掲載しています。初めてご覧になる際には、会員登録(無料)をお願いいたします。


![[Osaka Marriott Miyako Hotel] Plenty of cheese! Italian buffet held company release | Nikkan Kogyo Shimbun electronic version](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/28/1061eb31530c979d7b766ae1877b113a_0.jpeg)




