Security information for secure digital utilization provided by Canon MJ Cyber Security Information Bureau ESET 15-year attack method of malware framework targeting air gap network
The air gap is one of the security measures used to protect the most sensitive networks by physically isolating them from networks such as the Internet and insecure LANs. In the first half of 2020 alone, four previously unknown malicious frameworks have been found aimed at breaking into the airgap network. ESET has a total of 17 frameworks so far. ESET Research has re-examined each of the frameworks it knows so far, compared their attack methods and put them together in a white paper (English only).
Key points of the white paper:
This white paper describes how malware frameworks target air gap networks work and compares the characteristics of TTP in each framework. It also describes the main attack techniques of all malicious frameworks identified to date, as well as detection and defense that can help protect the airgap network.
ESET has conducted an analysis to gain technical details, using information revealed by more than 10 organizations in years of research. This will give you a comprehensive understanding of the malware framework and improve the security of your airgap network. In addition, we have summarized some points that may help you improve your ability to detect and defend against future attacks.
After a thorough investigation this time around, it turns out that even frameworks created 15 years ago have some big things in common. In this study, in particular, the malware execution mechanism used by both connected and airgap systems in the target network and the features of the malware in the airgap network (resident, reconnaissance, spread, spying, etc.) We also sought to clarify the sabotage that has been identified in at least one case). It also revealed the communication and data transfer channels used to control components running in fragmented and isolated networks with air gaps. We also systematically analyzed and documented the results to make it easier to identify and understand airgap malware that may be detected in the future.
Although all the frameworks we investigated had some differences and subtle differences, we focused on the implementation method in this analysis because of the inherent constraints of the airgap environment. It reveals how different these elements are. Based on the information obtained from these investigations, we will show you how to detect attacks on the air gap network that have been confirmed in the real environment.
The purpose of ESET's publication of this report is that many theoretical air-gap network attack methods have attracted attention in recent years, even though they have never been used in actual attacks. However, before considering how to deal with them, it is important to establish a defense system to properly defend the attack methods that have been confirmed so far and are used in virtually all frameworks. It is to make people understand that.
Victimology, attacker profile, timeline
An air gap network is a network that is physically isolated from other networks for added security. The air gap is a technique used to protect networks that interconnect the most sensitive and valuable systems. The air gap network is inevitably the target of many attackers, such as the APT group.
It can be argued that all attackers operating known malware frameworks designed to attack air gap networks belong to the APT (Persistent Targeted Attacks) group. These frameworks are used by various cybercriminal organizations, but all organizations have in common that their purpose is espionage.
Organizations using some frameworks may be clearly identified, as shown in the figure below.
There are also frameworks that are not clearly attributed and are the subject of speculation and debate. For example, Agent.BTZ was thought to belong to the Turla group, but some experts have different views.
Here are three typical frameworks that were the subject of this survey. These frameworks are described in a document leaked from Vault 7, and it is explained that they were in operation between 2013 and 2016, but no specimens that can be actually analyzed have been found.
The figure below shows the duration of each framework's activity retroactively, along with the time of the first published report. You can see that some frameworks have been active for several years before being detected. This shows how difficult it is to detect such a framework.
The activity period is specified from the published information. In some cases, the facts observed by the researcher could not determine the exact duration of activity, but in some cases they are estimated or inferred from rational hypotheses.
Figure 1: Period of activity of all known frameworks and dates published in the first published report
Air Gap System Analysis-From a Malware Perspective
To attack or compromise a system in an airgap network, you must develop the ability of attack tools to communicate over channels that are not normally used to operate the system. This is clear because the air gap network is isolated from the Internet.
Technically speaking, there is no exact definition of "air gap malware". For this reason, various discussions took place within ESET. Finally, in line with the purpose of this report, we have defined the malware that attacks the air gap network as follows.
Malware that implements a two-way (command transmission and response) or one-way (data leakage) secret offline communication mechanism between the air gap system and an attacker, or a malware component that operates in combination. Set (framework).
ESET has broadly categorized these frameworks into two categories: connected and offline. Almost all frameworks are designed to allow end-to-end remote connectivity between an attacker and a compromised system on the side of the airgap network. ESET calls this a "connected framework". The mechanism of this framework is shown below.
Figure 2: Overview of the components and actions of a connected framework designed to attack air gap networks.
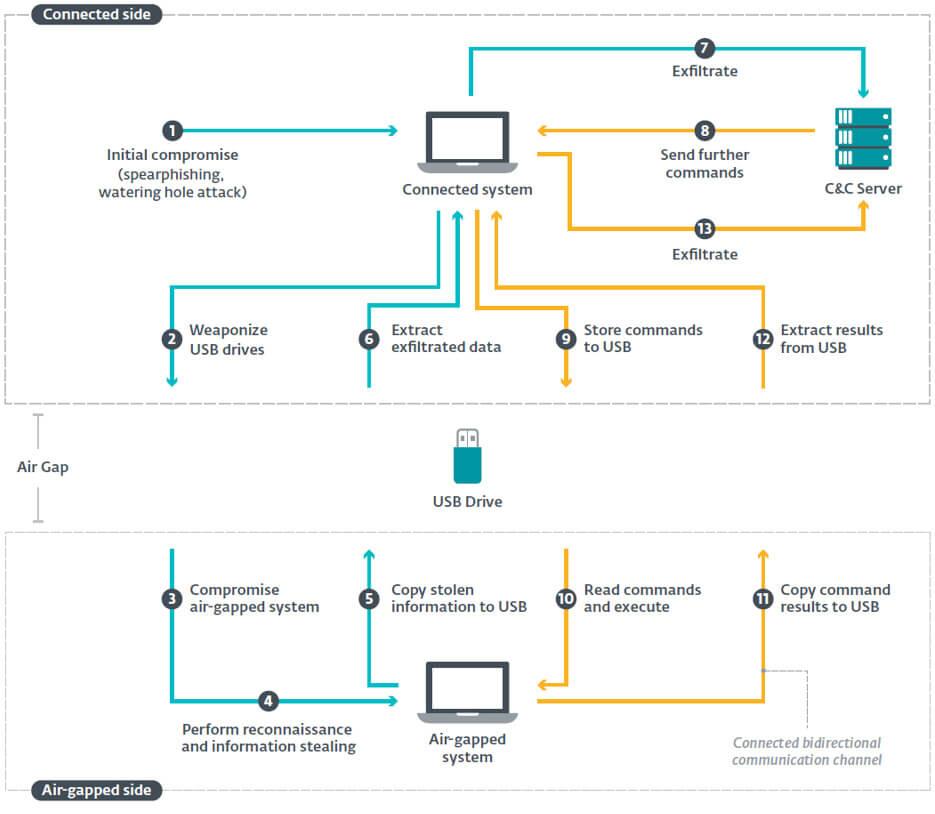
The most basic connected framework implements only the ability of an attacker to connect online to leak data to the outside world. The most powerful framework supports bidirectional communication protocols (yellow arrow). The attacker sends a command to the malware deployed on the air gap network via the compromised system on the connecting side. This command is often run from a secret communication channel configured on the USB drive. With this mechanism, an attacker is remotely executing arbitrary code on the air gap network.
In rare cases, there are attack scenarios that do not use a system that connects to the Internet at all. ESET calls this an "offline framework". In such cases, there is an operator or internal collaborator somewhere in the organization that is acting on behalf of the connectivity features normally found in connected frameworks. For example, prepare a malicious USB drive to run malware on the airgap side, run the malware on the airgap system, extract the collected data from the USB drive, or add it to the airgap side system. Send commands.
Figure 3: Overview of the components and actions of an offline framework designed to attack air gap networks.
This well-defined definition allows you to compare key features that are common to all frameworks.
How to execute an attack on the connection side
In the case of connected frameworks, in order to compromise the security of the air gap network, it is first necessary to establish a foothold for attacks on the system connected to the Internet. For APT, it may not be possible to pinpoint the exact source of the attack. However, the cases we have seen so far use the same techniques found in common malware, such as malicious attachments and links, and emails with USB worms.
First attack method on the air gap side
The question of how an attacker is executing malicious code in an airgap system is one of the most important issues in this investigation. Some frameworks use their own techniques, but what they all have in common is that they use a weaponized USB stick. The big difference between connected and offline frameworks is how to weaponize a USB drive. Connected frameworks typically monitor the insertion of new USB drives and deploy components to the connected system to automatically deploy the malicious code needed to compromise the security of the airgap system. The offline framework, on the other hand, assumes that the attacker will weaponize his USB drive. Interestingly, these frameworks have used various techniques over the long term to execute payloads on the target system. These methods can be broadly classified into three types.
Table 1: The first method to compromise the security of an air gap system
Functions performed on the air gap side
ESET investigated the three most important framework features available in the airgap side system: resident, reconnaissance and intelligence, diffusion and horizontal movement. As a result, it became clear that there are significant differences between frameworks in terms of operational objectives and complexity. For example, some frameworks were created for surprise attacks, where the task of stealing files is hard-coded, but the resident mechanism is not implemented, while others are resident without being detected by sophisticated methods. There was also a framework that implemented a mechanism to effectively spread in an air gap network. See Section 4.3 of this white paper for more information.
Channel for communication and data leakage to the outside
This is the most important characteristic in studying malware that attacks air gap networks. In this blog, we have clearly defined "air gap malware" and divided the framework for attacking the system on the air gap side into two categories, "connected" and "offline".
There is a big difference between the two functions of communication and data leakage to the outside in these two categories. In the online framework, as shown in the figure below, the communication channel with the online conventional C & C that connects the attacker and the compromised host on the connecting side, and the compromised host and air gap system on the connecting side. Requires an offline communication channel to connect to.
Figure 4: Online and offline communication channels in the connected framework
The offline framework, on the other hand, requires only offline communication channels (see figure below).
Figure 5: Offline communication channels in the offline framework
Offline communication channels are at the heart of the definition of air-gap malware. Using this communication channel, malware bypasses the defense layer of the airgap system, interacting with the targeted network, and in some cases only collecting information.
Offline channels are specific communication protocols that are performed in airgap systems using specific physical data transfer media.
Perhaps the first question about an attack on an airgap network is how to access an isolated airgap system? In fact, new research on physical data transfer media that has not been revealed so far is also published regularly. One of the most active researchers in the field is Mordechai Guri, senior researcher in cybersecurity at Ben Gurion University of Negev in Israel. Guri and his team have demonstrated that many techniques for transferring information from systems isolated in an air-gap environment are possible. These techniques can be used in a variety of attacks, with different bandwidths available.
It has been pointed out that attacks using such techniques have been confirmed in the real environment, but there are no cases where security industry experts analyze and publish the findings. Malicious frameworks targeting airgap networks that have been published so far use USB sticks as the physical data transfer medium for transferring information from the airgap system.
The following table shows that about half of the frameworks implement only one-way protocols. In such an attack scenario, information only flows from the compromised airgap system to the attacker, and no information flows from the attacker into the airgap system. That is, the malware component running on the airgap side does not implement a mechanism for updates or backdoor functionality, but performs certain hard-coded tasks (usually reconnaissance or information theft) and that information. Is designed to be returned to an attacker via a USB drive. An attacker cannot send updates or commands to control the compromised system.
A framework that implements a bidirectional protocol gives an attacker the flexibility to control the host on the airgap side. Interestingly, not all frameworks that implement bidirectional protocols take full advantage of this feature. In reality, it only implements a few fixed commands, such as stealing files that match a particular pattern or executing a particular file that resides on a USB drive.
Table 2: Types of offline communication protocols
Air gap network protection
Protecting airgap networks from cyberattacks is a very complex subject and requires a high degree of expertise in a number of disciplines. This report does not claim that ESET has a magical way to solve this problem. However, you need to understand how known frameworks work in an airgap environment and consider how to detect and block common malicious activity.
Section 5 of this white paper provides information to help you detect and block malicious activity that is common to many of the frameworks investigated and researched. These defenses are nothing new. ESET advocates a data-based approach. We hope that these approaches will help you prioritize the implementation and construction of defenses. It is important to build a system that can defend against known malware techniques, rather than spending valuable effort to thwart techniques that have never been abused in the real world.
Conclusion
There are two frameworks that attack the air gap network: the "connected framework" that is operated completely remotely, and the "offline framework" that relies on human resources such as insiders in the environment for some operations. It can be divided into two. Various techniques are used to initially access the airgap system, spread attacks within the network, and leak stolen information to the outside world, but the common purpose of all frameworks is. , It is nothing but spying on the target.
Detecting and analyzing such frameworks is an important issue. These frameworks can consist of multiple components. All components need to be analyzed together to get a complete picture of the actual attack.
Security vendors like ESET also use telemetry to detect new threats in systems running their products. However, systems operating within the airgap network do not transmit such telemetry. As a result, there is also the complication that it takes a long time to detect new malware targeting the air gap network.
Understanding how malware attacks air gap networks can help you establish and prioritize measures for detection and protection. For example, all frameworks use USB sticks in some way to spy on air gap systems. No framework uses a secret communication channel that requires protection against electromagnetic eavesdropping (TEMPEST).


![[Osaka Marriott Miyako Hotel] Plenty of cheese! Italian buffet held company release | Nikkan Kogyo Shimbun electronic version](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/28/1061eb31530c979d7b766ae1877b113a_0.jpeg)




